Phishing Awareness

Overview
This scenario-based course aims to raise employees’ awareness of phishing techniques and promote best practices for maintaining cybersecurity hygiene and protecting sensitive information within an organization.
Roles
Instructional Design, Visual Design
Tools
Articulate Rise, Canva, Powtoon, Inkscape, Miro, Powerpoint, Milanote, Revoicer
Try it!
Elearning Proposal
During the initial analysis, I identified a recurring issue found in many organizations: employees often lack awareness of phishing techniques, making them more vulnerable to cyber-attacks.
This project aimed to educate employees about phishing methods, particularly fraudulent emails, which are the most commonly used attack vectors against companies. Consequently, the target audience is broad and includes any employee within any organization.
To address this, I set two organizational objectives:
- Increasing employees’ awareness of various phishing techniques.
- Educating employees on how to effectively identify and avoid phishing attacks.
By the end of the course, participants must be able to:
- Describe common signs of phishing.
- Identify suspicious emails.
- Utilize best practices to avoid phishing attacks.
Design
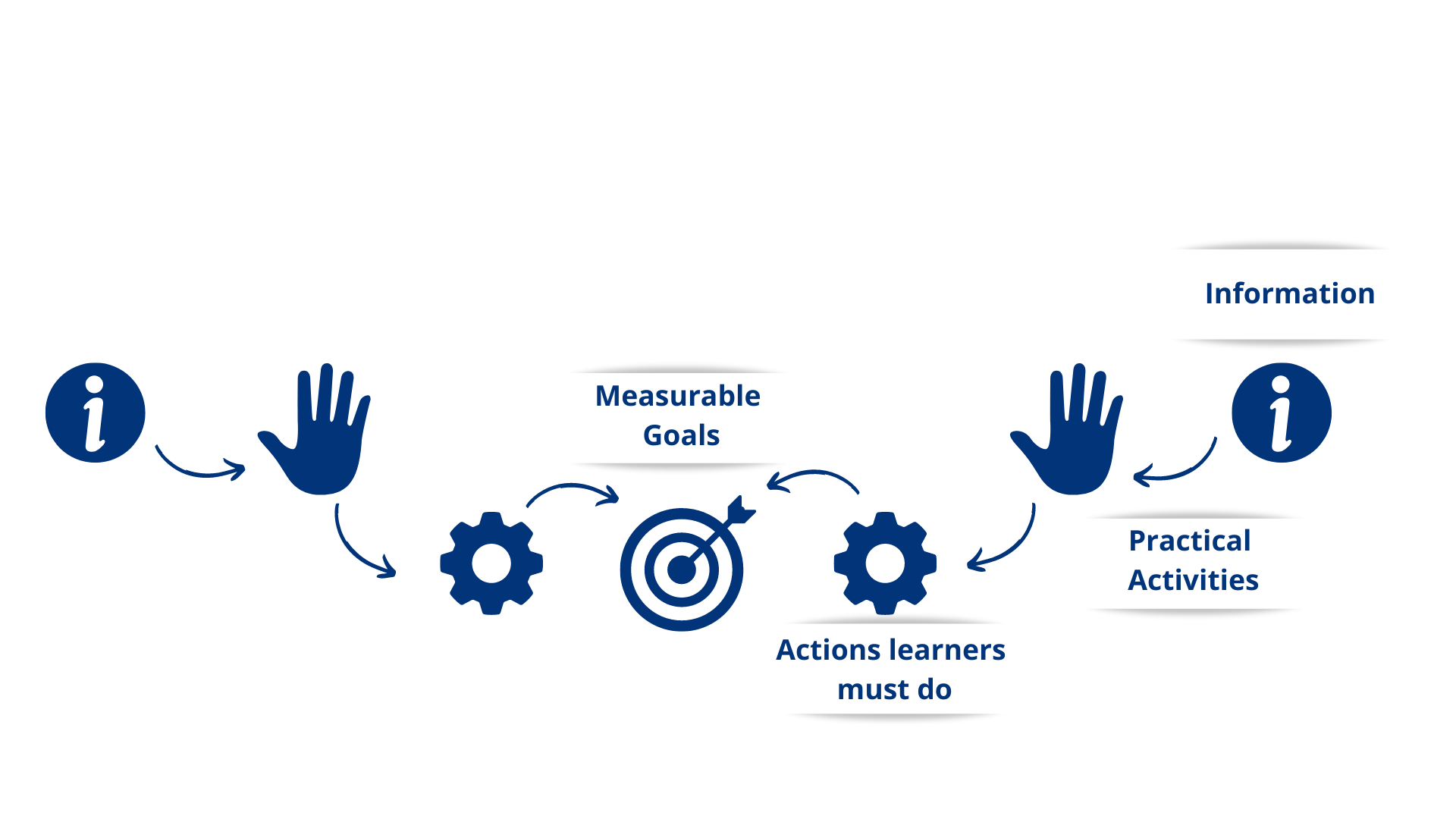
When designing the course, I was inspired by Cathy Moore’s action mapping, so I started by defining a clear and measurable business goal: to reduce the number of employees likely to fall for a phishing attempt.
I defined the actions learners should be able to accomplish at the end of the course, such as identifying suspicious emails and utilizing best practices to avoid phishing attacks. With these objectives in mind, I designed practical activities. And that led me to select the necessary information to provide and avoid overwhelming learners. This approach led to a self-paced, scenario-based learning experience.
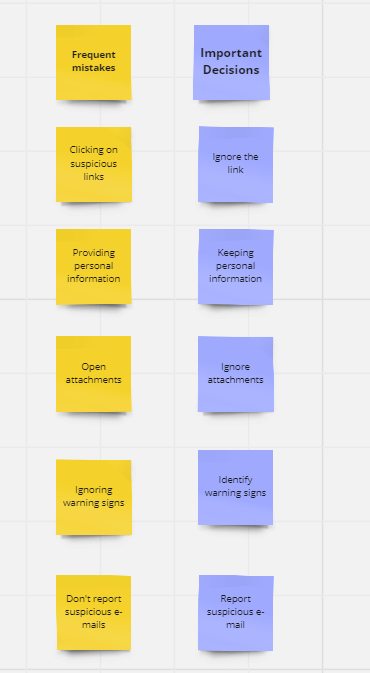
This led me to create a self-paced learning experience that integrated scenario-based training. To refine the acquisition of learners’ needs, I conducted extensive research by reading numerous articles and consulting a Subject Matter Expert (SME) working in the cybersecurity sector. With the collected information, I used Miro to identify common mistakes on one side and essential information on the other.
I wanted the course to start with a pre-assessment to determine if the learner had any prior knowledge of phishing, even a basic understanding. This would help better evaluate the knowledge gap at the end of the training.
Following the pre-assessment, I included a short video presenting the various phishing methods used by cyber-attackers to achieve their goals.
The course is divided into three parts, with the second part dedicated to email phishing, which was clearly identified by the SME as the main vulnerability in organizations.
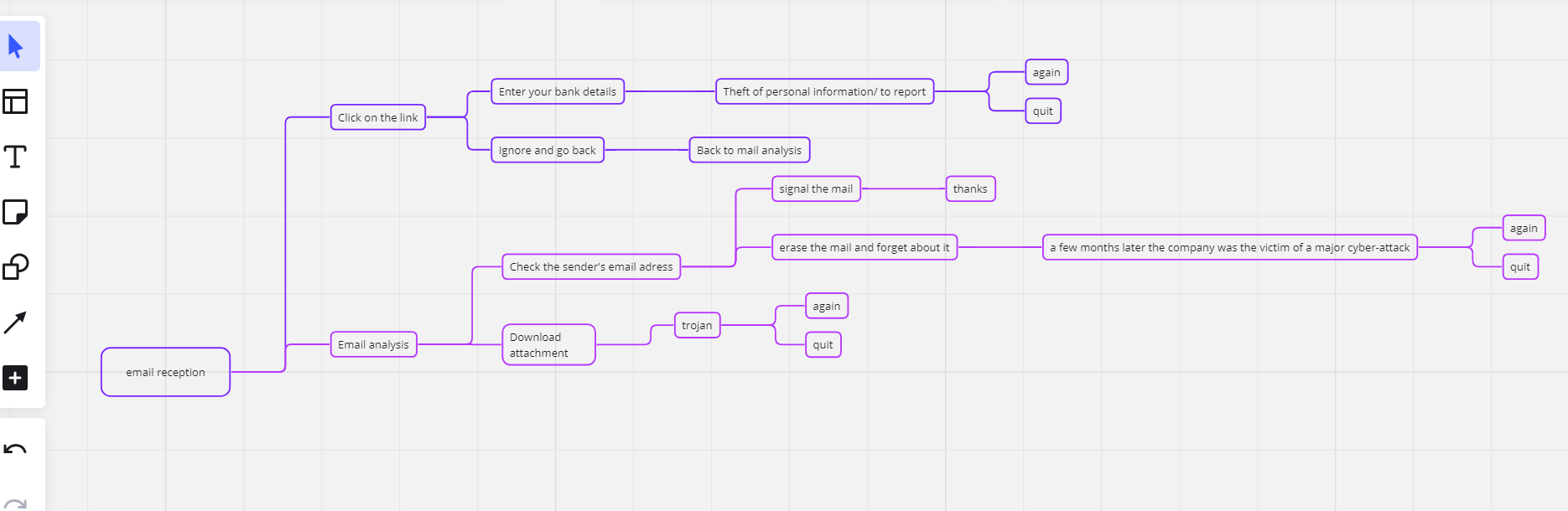
I chose to focus on one particular aspect of phishing to keep the information concise and enhance retention. For this, I opted for a scenario-based method, which is highly effective for learning as it directly presents the positive and negative consequences of actions, making the experience more memorable.
Miro was instrumental in mapping out the scenario branches, ensuring a coherent and interactive learning experience.
I formatted the course outline in a storyboard using PowerPoint, refining it through iterations based on feedback received from potential learners and the SME.
Visual Design
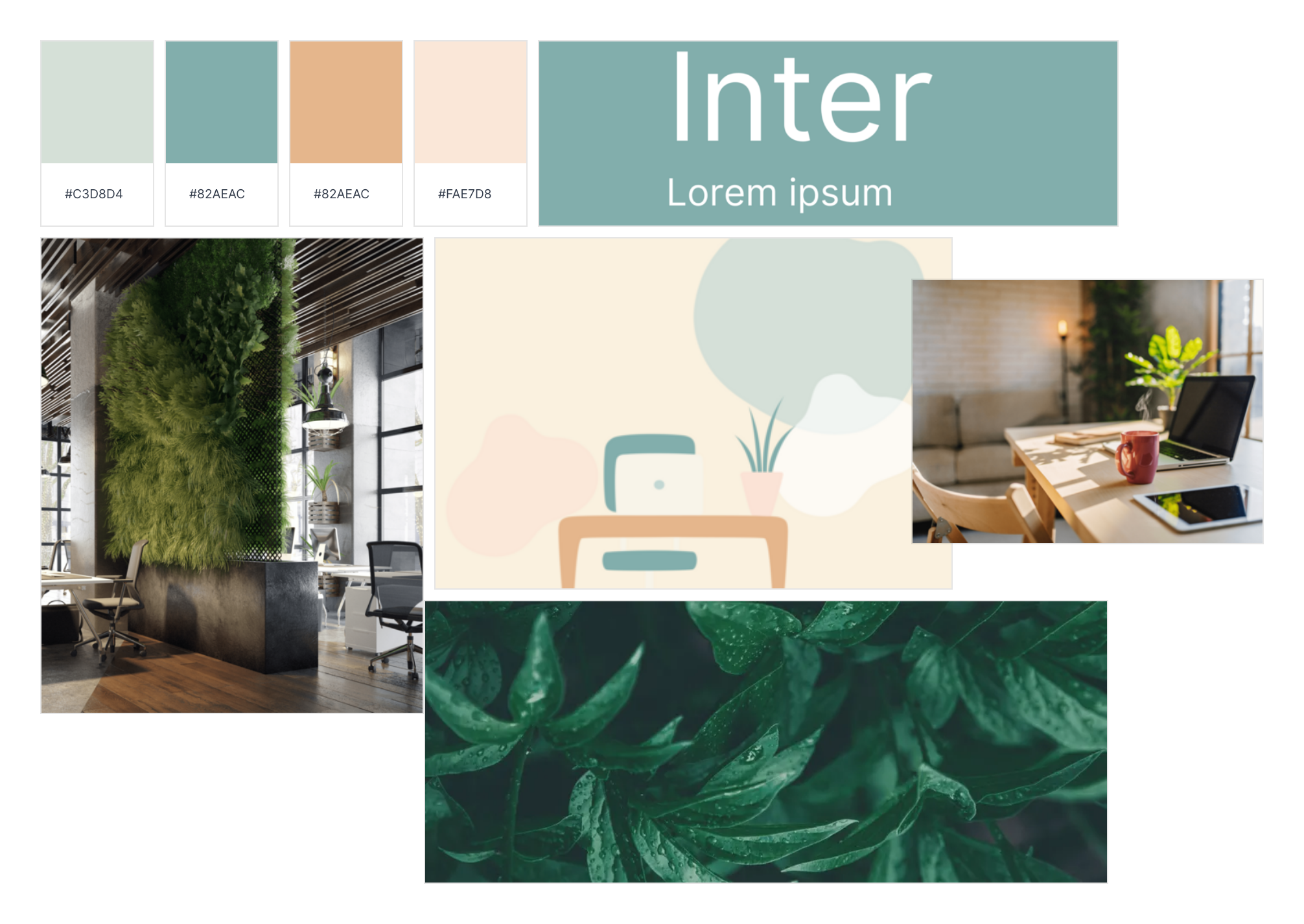
I created a mood board using Milanote to inspire and maintain overall coherence throughout the project. I sourced materials for the introductory video and modified them as needed using Canva and Inkscape.
Development
I developed a prototype and shared it with three members of the target audience as alpha testers. After integrating their feedback, I proceeded with full production. Upon completion, I published the project and thoroughly tested it for errors. I then conducted a final review by sharing the finished product with the SME.
Evaluation
If I had the opportunity to implement this course, an interesting approach to evaluate its effectiveness would be to conduct campaigns using fake phishing emails before and after the training. This would allow for a comparison of the number of employees who detect fake phishing attempts.
This key indicator could serve as a way to calculate ROI and determine if the training has impacted behaviors and produced the desired results.
To evaluate the course’s effectiveness, we can use other variables such as performance on assessments, course enrollment and attrition rates, and survey data with learner feedback at the end of the course.
This data would help identify trends, inform real-time adjustments, and guide broader course redesign efforts, ensuring that the course effectively meets its learning outcomes.
